
The real estate sector is a prime target for phishing attacks because it can involve the exchange of millions of dollars in a single transaction.
I wanted to share our experience on the growing threat of cybercrime in the real estate industry. In particular around the purchasing of a property and the risk of being defrauded in a Business Email Compromise (BEC) in which a conveyancer’s email can be compromised and settlement monies diverted.
This type of scam sheds light on how important it is for real estate businesses, brokers and conveyancers to maintain their cyber security, be cyber aware and ever vigilant for the safety of their clients who stand to lose significant sums in a single transaction.
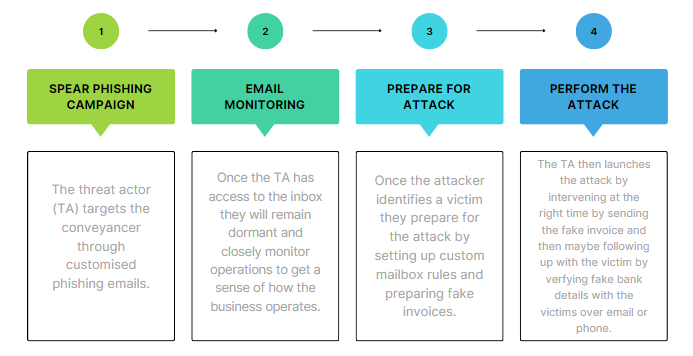
The flow diagram below shows the steps taken by a threat actor to gain unauthorised access to the conveyancer’s email account.
A thorough digital forensics analysis should focus on identifying potential entry points for the attacker/s, including, but not limited to, scrutinizing metadata within PDFs and analysing available Email logs, firewall logs, email headers, and an Internet Protocol analysis to piece together a comprehensive understanding of the intrusion. Additional considerations should be given towards small details, such as changes in communication patterns, language shifts, and variations in the timing of email transmissions to put together our report.
Recent matters have underscored the critical importance of ongoing cyber awareness. Even in routine transactions, reinforcing security protocols and procedures is paramount. A simple yet effective measure in this regard is for individuals to confirm their transactions by making a telephone call to the conveyancer before transferring a large sum of money and to not trust invoices or communications that are sent to them, even if it is from a known email address.
As we navigate the digital landscape, recent experiences have served as stark reminders of the persistent threat of cybercrime, especially in high-stakes transactions like real estate. Through a combination of digital forensics, incident response, and proactive cyber awareness, we can build resilience against evolving cyber threats.

